Laser Defender (FlyN Nick) Mac OS
- Posted by Kathy Patton, Apr 25, 2010 12:04 PM.
- Newsletter sign up. Take A Sneak Peak At The Movies Coming Out This Week (8/12) Billie Eilish drops the first track off upcoming album, and we’re ‘Happier Than Ever’.
Earlier this year, we announced the availability of Microsoft Defender ATP for Mac with preventive antivirus capabilities. With Microsoft Defender ATP for Mac, customers can better protect macOS endpoints, get these machines onboarded in the same portal as their Windows devices, and expand the single pane of glass experience to include macOS.
Windows 10 has crossed the halfway mark — more than 50 percent of desktops now run Microsoft’s newest operating system. The shift forms part of a larger pattern: As noted by recent survey data, more than three-quarters of companies cited “at least one innovative operational technology that they have adopted or are considering” in 2019.
The challenge? Increasing security risk. As network attack surfaces expand and operating systems are tasked to manage on-premises, cloud-based and even mobile deployments, the realities of risk come home to roost. Data confirms this concern, as 79 percent of companies rank cyber-risk as a top five concern even as their confidence to assess, detect and mitigate cyberattacks falls year over year.
To help strengthen and streamline security, Windows 10 includes new features that drive new operational best practices. Here’s what businesses need to know.
Windows 7 Security vs. Windows 10 Security: What’s the Difference?
Nick Cavalancia, Microsoft MVP and founder of Techvangelism, puts it simply: “Windows 10 security features are laser-focused on protecting and preventing current, specific forms of cyberattack.”
While popular predecessor Windows 7 prioritized “securing the endpoint,” Cavalancia notes that the focus was more general: “Keep the bad stuff from running.” Application, network and data protection simply weren’t part of the equation.
Windows 10 also takes a different approach to updates. By default, the OS automatically — and randomly, at least once every 17 to 22 hours — checks for new updates. Along with typical “patch Tuesday” updates that happen once per month, smaller security updates are deployed on an as-needed basis. Although absolute protection isn’t possible, this type of on-demand framework helps keep the largest number of devices current on updates and reduces overall risk.
Windows 10 Security Features: S Mode, Defender Security Center and More
What specific features are new in Windows 10 that support Microsoft’s general approach to security? It’s not a small list, but as Cavalancia points out, businesses will likely appreciate those features that help secure network environments against employees who are more focused on the task at hand than on defending network data. Some of the top features that “protect the user from themselves” include:
- Windows Defender Smart Screen — This protects users by blocking access to known, nonsecure sites.
- Windows Defender Application Guard — This makes it possible to access untrusted sites “but does so in an isolated virtual container, blocking access to system resources.”
- Windows 10 S Mode — Shadow IT remains alive and well — 76 percent of employees have accessed resources on work devices without IT permission. S mode helps control shadow IT sprawl by limiting app installation to those from the Microsoft Store.
- Windows Sandbox — If organizations choose to allow broader application permissions, Windows Sandbox ensures new apps run in isolated virtual containers to prevent full system access.
- Remote Desktop Biometrics — As noted by Cavalancia, “Remote desktop protocol (RDP) attacks are still one of the main ways ransomware attacks are initially carried out.” Windows Hello for Business leverages biometric authentication to reduce the risk of RDP compromise.
How to Manage Top Security Threats in Windows 10
For companies just making the move to Windows 10, it’s worth tackling the basics before moving on to more strategy-driven protection. Start with:
- Handling user accounts and identity — Deploying a combination of tools such as Microsoft Passport, Windows Hello and Microsoft Azure Active Directory helps limit potential use risk. Passport provides a multifactor password alternative, while Hello deploys biometrics and Active Directory takes identity and access management (IAM) into the cloud. Cavalancia makes it clear that “bad guys can’t do anything without credentials.” Leveraging Windows 10 tools to implement least-privilege protocols confounds most cybercriminal attacks.
- Securing physical devices — Here, it’s a good idea to implement UEFI Secure Boot and create a Windows 10 save point. Secure Boot helps maintain OS integrity by preventing hardware-based malware installations, while save points provide a safety net if new application installations go south.
- Protecting critical data — Microsoft BitLocker empowers configurable disk encryption, while Enterprise Data Protection tools permit integrated data separation and containerization along with file-level encryption to defend data at scale.
- Detecting new threats — Microsoft Defender tools, including Device Guard, allow businesses to lock down desktops and devices and compel applications to prove their trustworthiness, while the Windows Defender Security Center makes it easier for IT teams to control firewall, anti-virus and anti-malware solutions.
Windows 10 Implementation Guide: Cybersecurity Best Practices
Approach is everything. Even with the best tools available, businesses need to implement security best practices that align with both organizational goals and existing technology deployments.
First, define your update schedule. For business IT departments, there’s a tendency to avoid immediate updates in case the latest Windows version causes problems for current deployments — but waiting too long puts critical data at risk. Best bet? Find a middle ground. As noted by ZDNet, the Windows Update for Business lets IT teams defer quality updates for 30 days and feature updates for two years. Settle on a schedule that works for you — between seven and 15 days is often enough time to ensure there are no compatibility issues — and then stick to it.
It’s also a good idea to “look for ways to enhance existing security with Windows 10 integrated solutions.” While third-party tools can help address specific concerns, limiting the number of interlocking technologies on your network also limits the number of potential gaps.
Laser Defender (flyn Nick) Mac Os X
Finally, Cavalancia recommends that businesses “always, always, always think about security as a layered defense.” No single solution provides complete protection. By regularly assessing their security posture, companies can find critical weaknesses and identify the best solution — Windows or otherwise — to increase overall protection.
More On
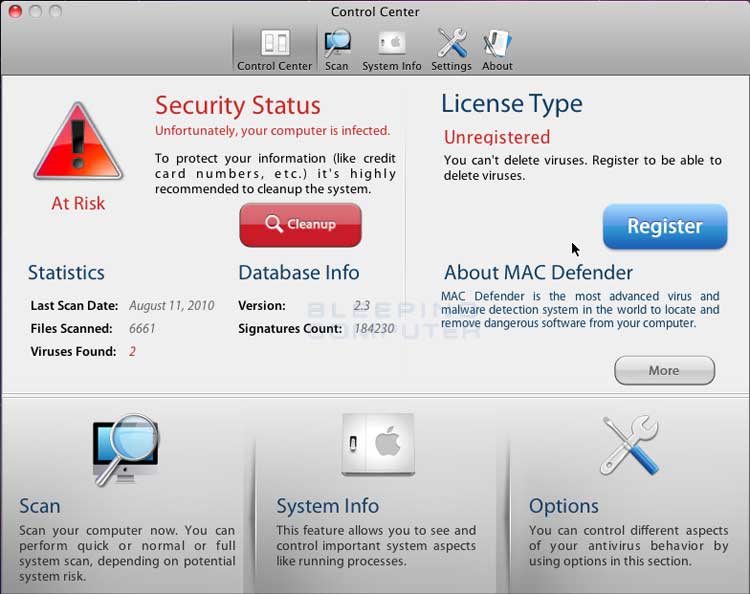
Mac Defender (also known as Mac Protector, Mac Security,[1]Mac Guard,[2]Mac Shield,[3] and FakeMacDef)[4] is an internet rogue security program that targets computers running macOS. The Mac security firm Intego discovered the fake antivirus software on 2 May 2011, with a patch not being provided by Apple until 31 May.[5] The software has been described as the first major malware threat to the Macintosh platform (although it does not attach to or damage any part of OS X).[6][7][8][9][10][11] However, it is not the first Mac-specific Trojan, and is not self-propagating.
A variant of the program, known as Mac Guard, has been reported which does not require the user to enter a password to install the program,[12] although one still does have to run the installer.[13]
Symptoms[edit]
Users typically encounter the program when opening an image found on a search engine. It appears as a pop-up indicating that viruses have been detected on the users' computer and suggests they download a program which, if installed, provides the users' personal information to unauthorized third parties.
The program appears in malicious links spread by search engine optimization poisoning on sites such as Google Image Search.[14] When a user accesses such a malicious link, a fake scanning window appears, originally in the style of a Windows XP application,[14] but later in the form of an 'Apple-type interface'.[15] The program falsely appears to scan the system's hard drive.[14] The user is then prompted to download a file that installs Mac Defender, and is then asked to pay US$59.95 to US$79.95 for a license for the software.[14] Rather than protect against viruses, Mac Defender hijacks the user's Internet browser to display sites related to pornography, and also exposes the user to identity theft (by passing on credit card information to the cracker).[14][16] A newer variant installs itself without needing the user to enter a password.[17] All variants require the user to actively click through an installer to complete installation even if a password is not required.[18]
Origin[edit]
The software has been traced through German websites, which have been closed down, to the Russian online payment ChronoPay.Mac Defender was traced to ChronoPay by the email address of ChronoPay financial controller Alexandra Volkova.[19] The email address appeared in domain registration for mac-defence.com and macbookprotection.com, two web sites Mac users are directed to in order to purchase the security software. ChronoPay is Russia's largest online payment processor. The web sites were hosted in Germany and were suspended by Czech registrar Webpoint.name. ChronoPay had earlier been linked to another scam in which users involved in file sharing were asked to pay a fine.[20][21]
Apple response[edit]
According to Sophos, by 24 May, 2011, there had been sixty thousand calls to AppleCare technical support about Mac Defender-related issues,[22] and Ed Bott of ZDNet reported that the number of calls to AppleCare increased in volume due to Mac Defender and that a majority of the calls at that time pertained to Mac Defender.[23] AppleCare employees were told not to assist callers in removing the software.[24] Specifically, support employees were told not to instruct callers on how to use Force Quit and Activity Monitor to stop Mac Defender, as well as not to direct callers to any discussions pertaining to the problems caused by Mac Defender.[22] An anonymous AppleCare support employee said that Apple instituted the policy in order to prevent users from relying on technical support instead of anti-virus programs.[24]
AppleCare employees were told not to assist callers in removing the software, but Apple later promised a software patch.[25] On 24 May 2011 Apple issued instructions on the prevention and removal of the malware.[26] The Mac OS X security update 2011-003 was released on 31 May 2011, and includes not only an automatic removal of the trojan, and other security updates, but a new feature that automatically updates malware definitions from Apple.[1]
See also[edit]
Laser Defender (flyn Nick) Mac Os Update

References[edit]
- ^ ab'About Security Update 2011-003'. 31 May 2011. Retrieved 31 May 2011.CS1 maint: discouraged parameter (link)
- ^'Intego Mac Security Blog'. 25 May 2001. Archived from the original on 27 May 2011. Retrieved 27 May 2011.
- ^'Mac malware morphs to 'MacShield''. Technolog. MSNBC. Archived from the original on 6 June 2011. Retrieved 5 June 2011.CS1 maint: discouraged parameter (link)
- ^'Threat Description: Rogue:OSX/FakeMacDef.A'. F-Secure. Retrieved 11 February 2013.CS1 maint: discouraged parameter (link)
- ^Hamburger, Ellis (2 May 2011). 'WARNING: This Mac App Is Stealing Credit Card Numbers'. Retrieved 7 December 2011.CS1 maint: discouraged parameter (link)
- ^'Macs face first virus threat'. techday.co.nz. 4 May 2011. Archived from the original on 9 October 2011. Retrieved 27 May 2011.
- ^'Say hello to MAC Defender, the first major widespread piece of Mac based malware'. left-click.us. Archived from the original on 26 June 2012. Retrieved 27 May 2011.
- ^Dachis, Adam (25 May 2011). 'How to Protect Your Computer from Mac Defender and Its Counterparts'. Mac Defender has been making a lot of noise as one of the first major Mac security threats. lifehacker.com.
- ^Dan Moren (2 May 2011). 'New Mac Trojan horse masquerades as virus scanner'. macworld.com.
- ^Trenholm, Rich (19 May 2011). 'The old saw that Macs don't get viruses is under fire as a piece of malware called Mac Defender is rampaging across the Web'. cnet.com.Missing or empty
url=(help) - ^'Mac Defender fake antivirus software is first major attack on Apple computers'. crave.cnet.co.uk. Archived from the original on 22 July 2011. Retrieved 27 May 2011.
- ^< 'Mac Guard: Apple users hit by second Mac malware scam'. Christian Science Monitor Horizons blog. 26 May 2001.
- ^'New Mac Defender Variant, MacGuard, Doesn't Require Password for Installation'. Mac Security Blog from Intego. 25 May 2011. Archived from the original on 27 May 2011. Retrieved 27 May 2011.
- ^ abcdeWisniewski, Chester (2 May 2011). 'Mac users hit with fake anti-virus when using Google image search'. Naked Security. Sophos. Retrieved 24 May 2011.CS1 maint: discouraged parameter (link)
- ^Mills, Elinor (19 May 2011). 'How bad is the Mac malware scare? (FAQ)'. CNET.
- ^Chen, Brian X. (19 May 2011). 'New Mac Malware Fools Customers, But Threat Still Relatively Small'. Wired. Condé Nast Digital. Retrieved 24 May 2011.CS1 maint: discouraged parameter (link)
- ^'New Mac Defender Variant, MacGuard, Doesn't Require Password for Installation'. The Mac Security Blog » INTEGO SECURITY MEMO. Archived from the original on 27 May 2011. Retrieved 27 May 2011.
- ^'New Mac Defender Variant, MacGuard, Doesn't Require Password for Installation'. The Mac Security Blog » INTEGO SECURITY MEMO. Archived from the original on 27 May 2011. Retrieved 27 May 2011.
- ^'Apple takes on Mac Defender Scam'. International Business Times. 29 May 2011.
- ^'MacDefender Scareware Linked to Russian Payment Site'. News & Opinion. PCMag.com.
- ^'Russia's ChronoPay Executive Linked to Mac Defender Scam'. International Business Times.
- ^ abWisniewski, Chester (24 May 2011). 'Apple support to infected Mac users: 'You cannot show the customer how to stop the process''. Naked Security. Sophos. Retrieved 24 May 2011.CS1 maint: discouraged parameter (link)
- ^Bott, Ed (18 May 2011). 'An AppleCare support rep talks: Mac malware is 'getting worse''. ZDNet. Retrieved 24 May 2011.CS1 maint: discouraged parameter (link)
- ^ abCluley, Graham (18 May 2011). 'Malware on your Mac? Don't expect AppleCare to help you remove it'. Naked Security. Sophos. Retrieved 24 May 2011.CS1 maint: discouraged parameter (link)
- ^'Mac malware authors release a new, more dangerous version'. zdnet.com. 25 May 2011.
- ^'How to avoid or remove Mac Defender malware'. 24 May 2011. Retrieved 1 June 2011.CS1 maint: discouraged parameter (link)